HFS Research Podcast: The Next Wave with Bill...
Bill McDermott (Chairman and CEO of ServiceNow) and Ravi Kumar (CEO of Cognizant) join HFS Research Chief Analyst Phil Fersht to explore how AI is revolutionising enterprise...
Read MoreThirdera generates transformation, digitisation, and automation for our customers at the speed of NOW.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.

.jpg?width=500&height=276&name=filter%20group%20of%20people%20at%20desk%20laptop%20laughing%202021-10%20(1).jpg)


Insurance Provider Projects $75MM Gain in Business Value from Asset Management Transformation
Read more
.jpg?width=500&height=276&name=Multichannel%20pipette%20tips%20reaction%20mixture%20plastic%20wells%202022-05%20(1).jpg)
.jpg?width=500&height=276&name=group%20-%20statistical%20analysis%202023-03%20yellow%20pink%20(1).jpg)
Balancing mission-driven goals with operational efficiency requires innovative solutions that can streamline processes and enhance programme delivery without straining budgets.

UN Agencies Rely on Thirdera and ServiceNow to Support the Ukrainian Aid Response
Read moreDigitise and automate workflows to enhance the customer experience, online and in-store.

.jpg?width=500&height=276&name=Servers%20data%20center%20room%20with%20bright%20speed%20light%202022-05%20(3).jpg)
Global SAP on Cloud Leader, Lemongrass, Embarks on Multi-Continent ITSM Overhaul
Read more

Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
With cybersecurity spending estimated to be $172 billion in 2023, security teams are under pressure to deliver more for the money being spent. Many companies have a variety of tools in use to manage their cyber-attack surface, including Vulnerability Scanners like Qualys and Rapid7 InsightVM, Static and Dynamic Application Security Testing tools like Veracode, and Secure Configuration Assessment tools like Tanium Comply. All these tools help organisations to understand their security posture and to work to reduce the risk of attack.
However, when working with multiple disparate tools they may not all have the same information about potentially impacted devices or applications which may require remediation teams to research the impacted system before being able to start remediation. Additionally, as these technologies may not gather all the same information about impacted systems, it can be hard to understand everything that exists in your environment to even know what needs to be secured.
To understand what exists in your environment a Configuration Management Database (CMDB) comes into play. Many companies have a rudimentary CMDB that may not have a high level of trust around accuracy. And while many people understand the value of the CMDB, getting funding to help build, maintain, and mature it can be tough to find. In recent years though, cybersecurity programs have been able to drive and fund CMDB work as you can’t secure something if you don’t know you have it. However, shepherding a successful deployment is an entirely different challenge addressed in our recent blog Four Steps to a Successful ServiceNow CMDB Deployment.
Populating the CMDB allows for a variety of benefits when looking at vulnerabilities and configuration errors. Tracking ownership data in the CMDB such as the group that owns the system allows you to automatically assign work to the correct teams so it doesn’t have to be triaged and starts off at the team that can address it.
Tracking relationships in the CMDB between devices and applications or services can extend assignment routing to assign to an application or service support team instead of a device.
The other major benefit to the CMDB is the ability to help determine the risk of findings on a system. A comprehensive Risk calculation considers three categories of risk factors, as shown below. Inherent risk factors come from scanners or static sources (e.g. CVSS score from the NVD) to determine the general risk to any/all organisations. Company-specific risk factors are found in the CMDB and provide system-specific context to the finding based on what is known about the impacted system and its use in the larger environment. And finally, Temporal risk factors are focused on whether the risk is actively being exploited and any active campaigns. Integration with data sources like the CISA Known Exploited Vulnerabilities Catalog can help to identify temporal risks.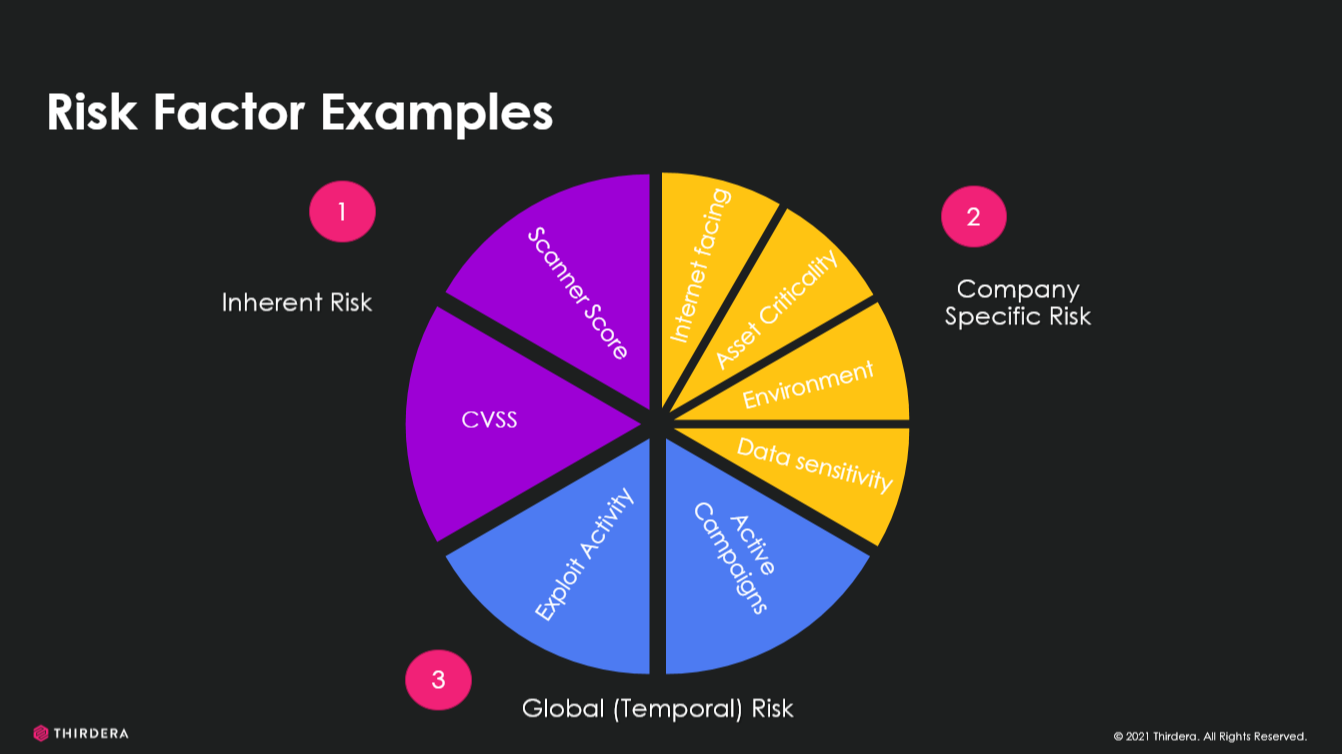
Because the CMDB has relationships between systems and applications, you can populate some of the key risk factors such as whether a system is internet-facing or has sensitive data on it at the application or service level, and set the risk for associated systems based on that higher level application. If your CMDB doesn’t have those relationships yet, you can also set the risk factors directly on the systems impacted (servers, workstations, switches, etc.).
When looking at potentially millions of findings to address, being able to automatically calculate risk based on environmental factors can expedite remediation by getting the more crucial items to the remediation teams as quickly as possible.
There are many ways to populate the CMDB, depending on your organisation’s starting point and available tools and resources.
ServiceNow Discovery can discover your entire IT infrastructure by scanning ranges of IP addresses as well as using Cloud Discovery to connect to your public and private clouds to ingest cloud-based infrastructure. Service can discover application services and build a comprehensive map of all devices, applications, and configuration profiles used.
Service Graph Connectors can be used to pull in asset/configuration data from a variety of device management, patching, and monitoring tools such as Microsoft SCCM, SolarWinds, and Jamf. There are currently about 40 Service Graph Connectors available in the ServiceNow Store.
In addition to your cybersecurity tools detecting vulnerabilities and misconfigurations, most track at least some rudimentary data about the systems they scan such as IP addresses, hostnames, cloud identifiers, and fully-qualified domain names. Most of the available scanner integrations for Vulnerability Response and Configuration Compliance will pull at least that minimum set of data into your ServiceNow instance, compare it against anything existing in the CMDB and if no matches are found will create a new configuration item.
In addition, many of these tools, such as Qualys and Rapid7 have pre-built CMDB-specific integrations that may be able to populate more robust data into the CMDB that can then be matched from the scanner integrations.
If you’re looking to start using ServiceNow’s Security Operations applications but don’t have a CMDB yet, or don’t have a quality CMDB, don’t feel discouraged. Thirdera works with you to bring your resources together with the ServiceNow platform, allowing you to synchronise Security Operations data into one solution and make decisions based on their impact to your business.
As mentioned, ServiceNow can ingest data from your cybersecurity tools to help build out your CMDB in addition to the other options above. You may end up pulling in many unknown systems that have vulnerabilities that can take some time to investigate, but it’s still better to know what is out there. And having unknown systems coming into the CMDB is often the driver to look at what else can be done to improve the CMDB.
If you already have a CMDB but want to understand how healthy it is and get recommendations on the next steps in your CMDB journey, contact us about a CMDB Assessment.
Bill McDermott (Chairman and CEO of ServiceNow) and Ravi Kumar (CEO of Cognizant) join HFS Research Chief Analyst Phil Fersht to explore how AI is revolutionising enterprise...
Read MoreAs artificial intelligence (AI) and machine learning (ML) continue to transform entire industries, organisations increasingly need robust governance and visibility into these...
Read MoreArtificial intelligence (AI) is changing how we interact with technology, driving improvements in business processes and customer experiences. Two of the most talked about...
Read MoreOriginally introduced in ServiceNow Utah, Application Portfolio Management (APM) was a part of the Strategic Portfolio Management (SPM) toolset. APM offered the capability to...
Read More